Building Home Lab for Pentest [Vulnerable AD Server] – Part 2
Active directory is back bone of any organization. Understanding how its built, and how to test for vulnerabilities is crucial to securing your client. In this post we will create a AD server to test for basic vulnerabilities like Anonymous LDAP, queryAbusing ACLs/ACEs, Kerberoasting, AS-REP Roasting etc.

In this Post we will cover:
- This is a follow up from previous post: Part 1
- How to setup Windows 2019 server on Virtual Box
- Set up a vulnerable AD server
- Basic AD pentest
AD Server Setup
We will download Windows Server 2019 Virtual Box file for easy installation:
https://www.microsoft.com/en-in/evalcenter/download-windows-server-2019
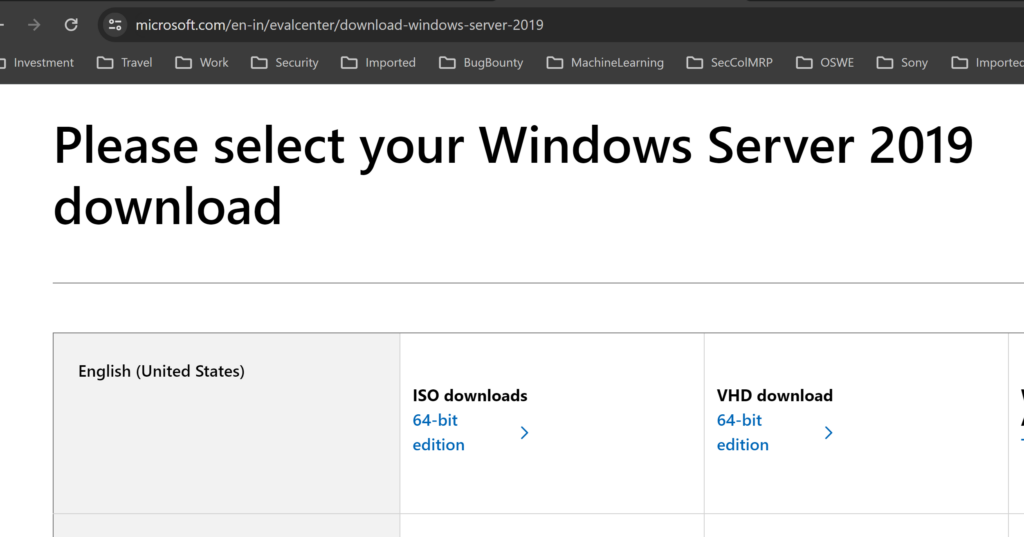
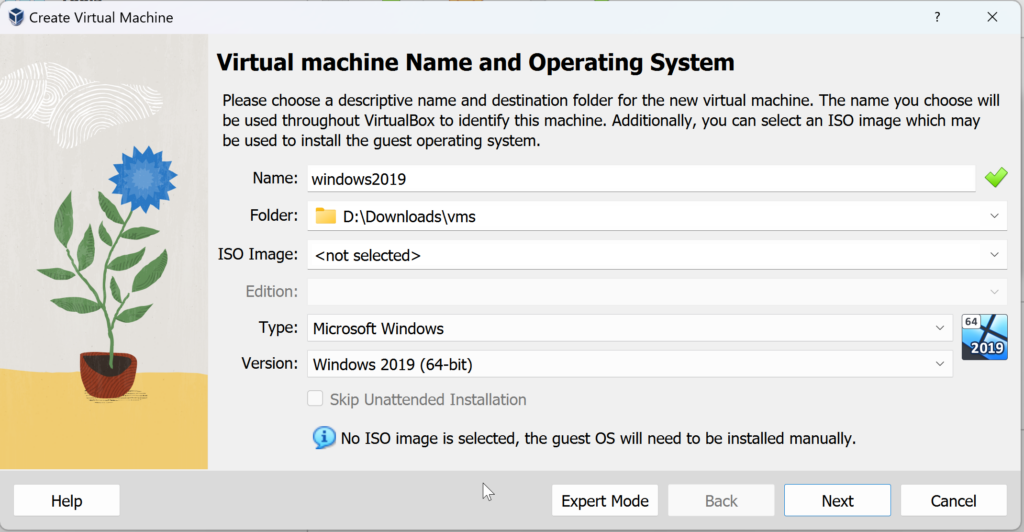
As in part 1, we will create Windows Virtual machine:
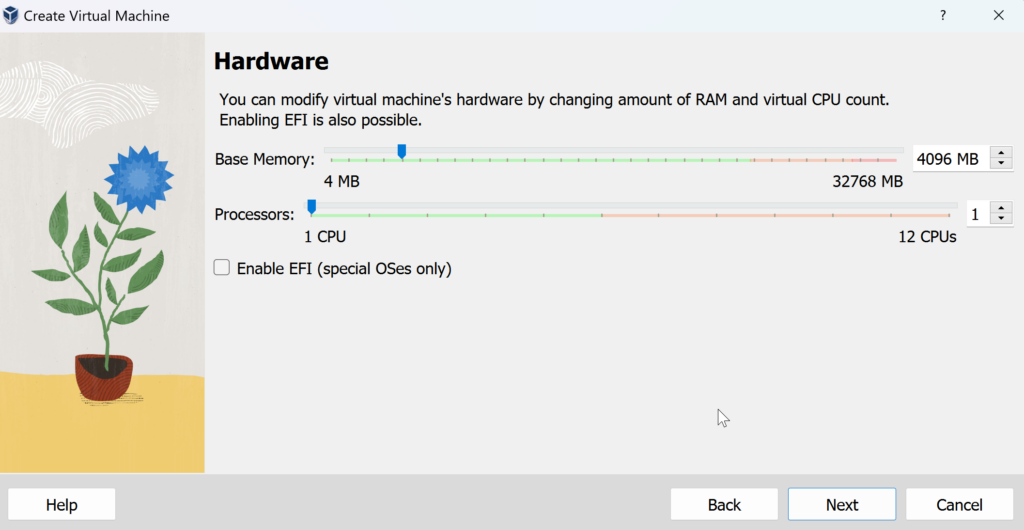
Let us assign 4GB RAM for faster operation
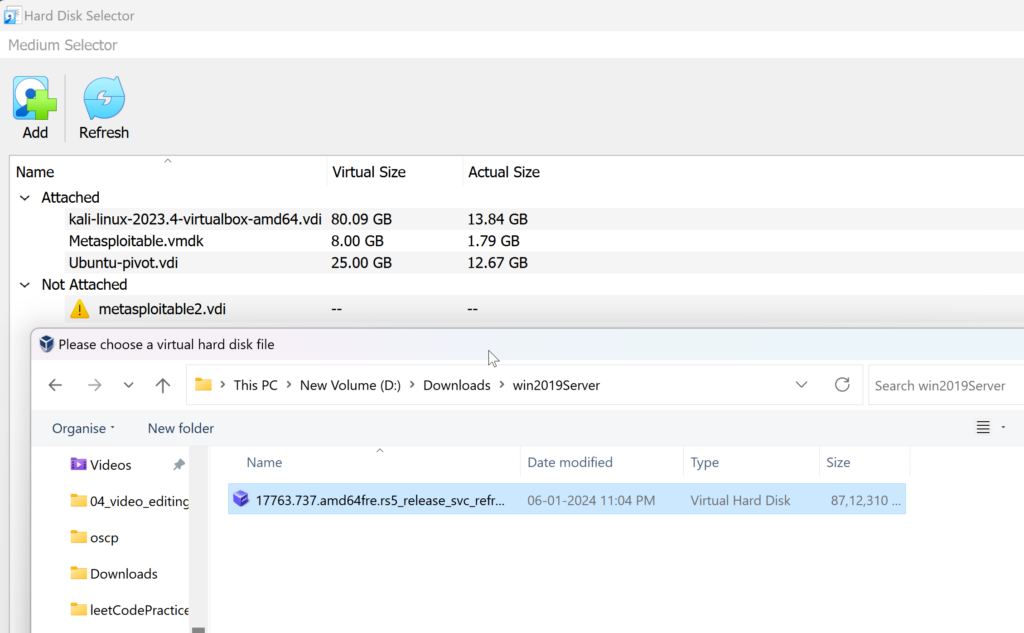
Add hard disk device, and select Windows 2019 image.
In next window, select ‘Use an Existing …’
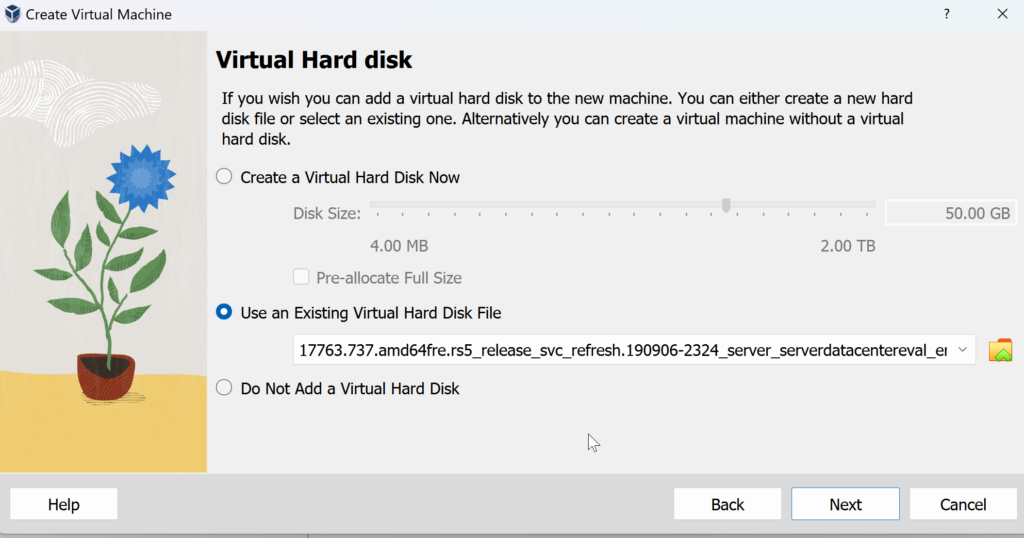
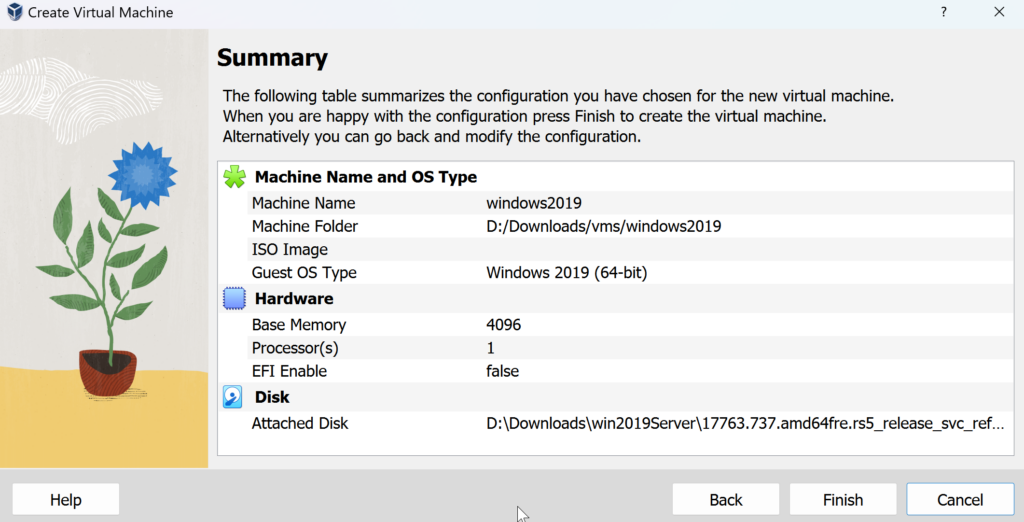
Review the settings and finish the setup
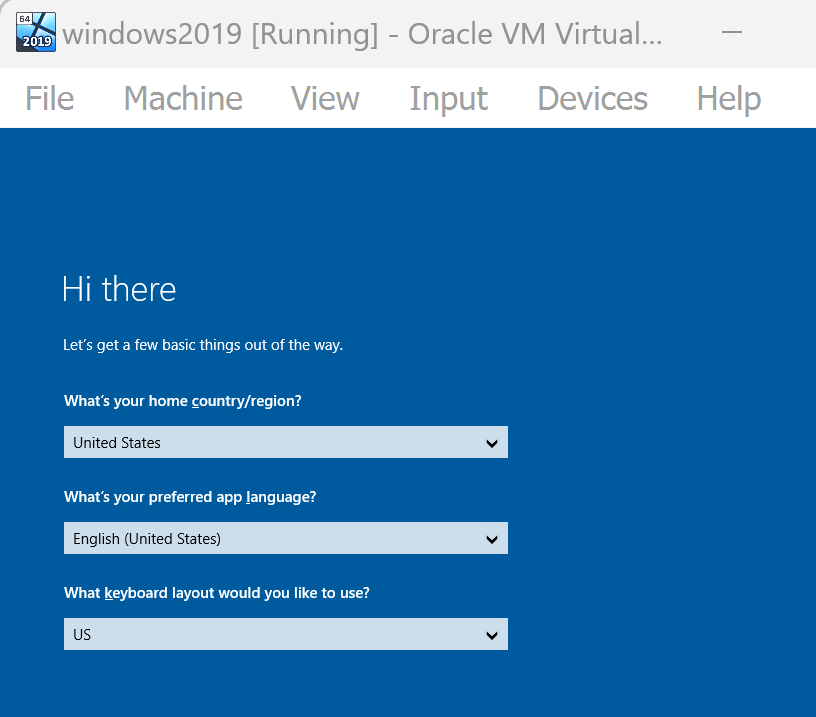
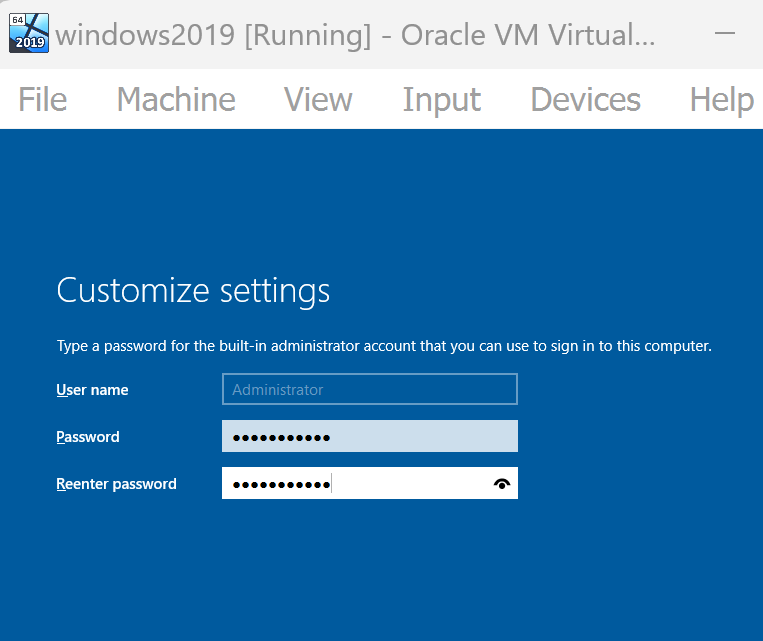
After starting the VM, you must see following window, select your preference. Set the password to Password123!
You can create a snapshot now, in case things go south, we can always revert back to this image.
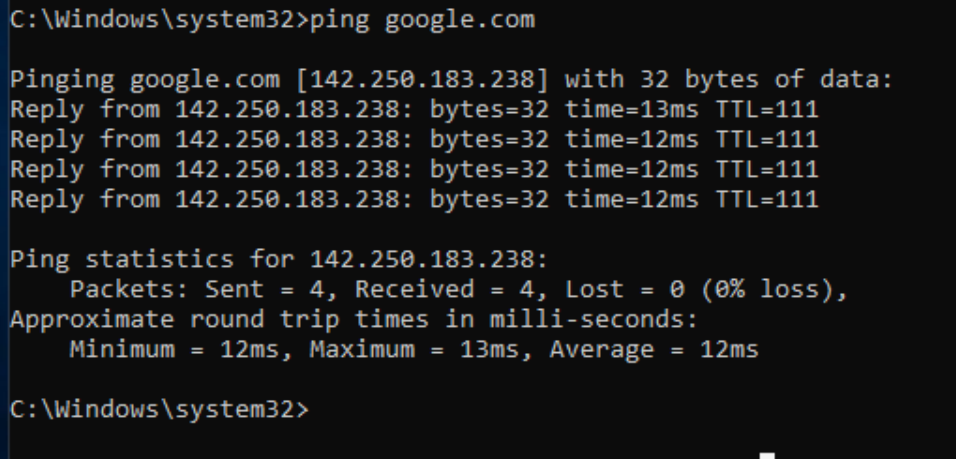
Lets check if we can connect to the internet, lets ping google.
Vulnerable AD script
We will use following script to create vulnerable AD Server: https://github.com/WaterExecution/vulnerable-AD-plus
Let us first bypass execution policy so that we can run other powershell scripts:
Set-ExecutionPolicy -ExecutionPolicy Bypass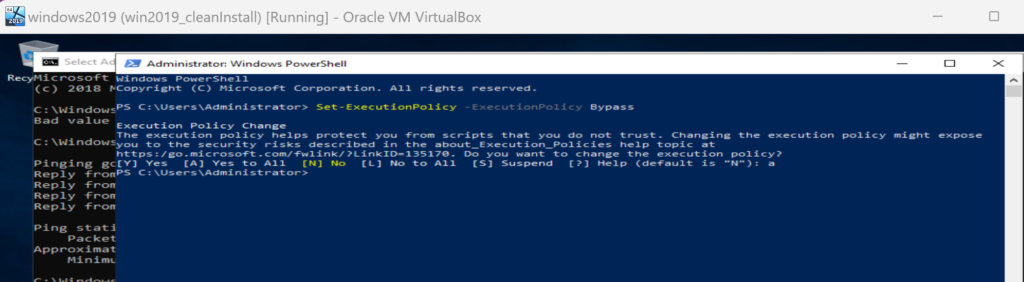
First, we install Active Directory Domain Services
Install-windowsfeature AD-domain-services
Then import ADDSDeployment
Import-Module ADDSDeployment
Now we can run their script
Install-ADDSForest -CreateDnsDelegation:$false -DatabasePath "C:\\Windows\\NTDS" -DomainMode "7" -DomainName "change.me" -DomainNetbiosName "change" -ForestMode "7" -InstallDns:$true -LogPath "C:\\Windows\\NTDS" -NoRebootOnCompletion:$false -SysvolPath "C:\\Windows\\SYSVOL" -Force:$trueThe VM restarts after the script executes
Notice new login is created, login with password “Password123!”
Open powershell and enter the following script:
IEX((new-object net.webclient).downloadstring("https://raw.githubusercontent.com/WaterExecution/vulnerable-AD-plus/master/vulnadplus.ps1"));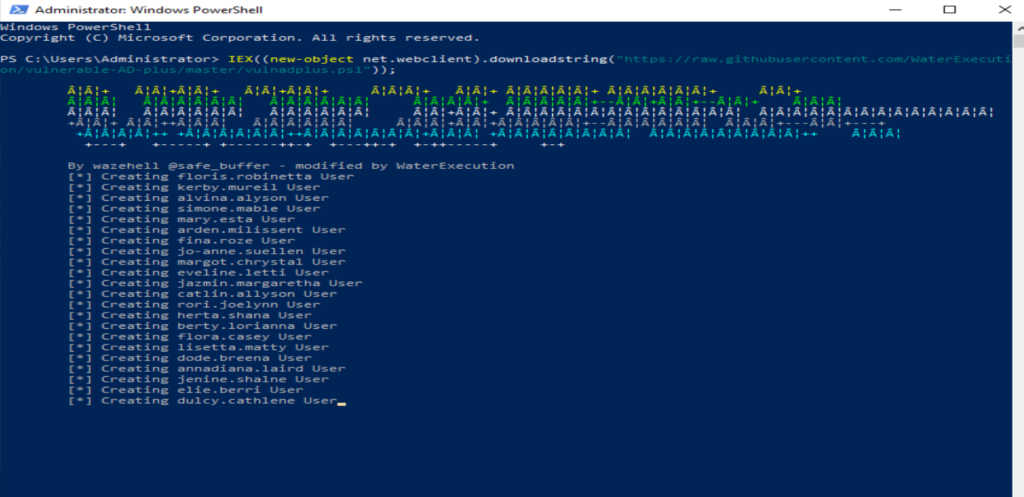
The system reboots after the script executes.
Pentesting AD
Now we can do some basic testing from Kali
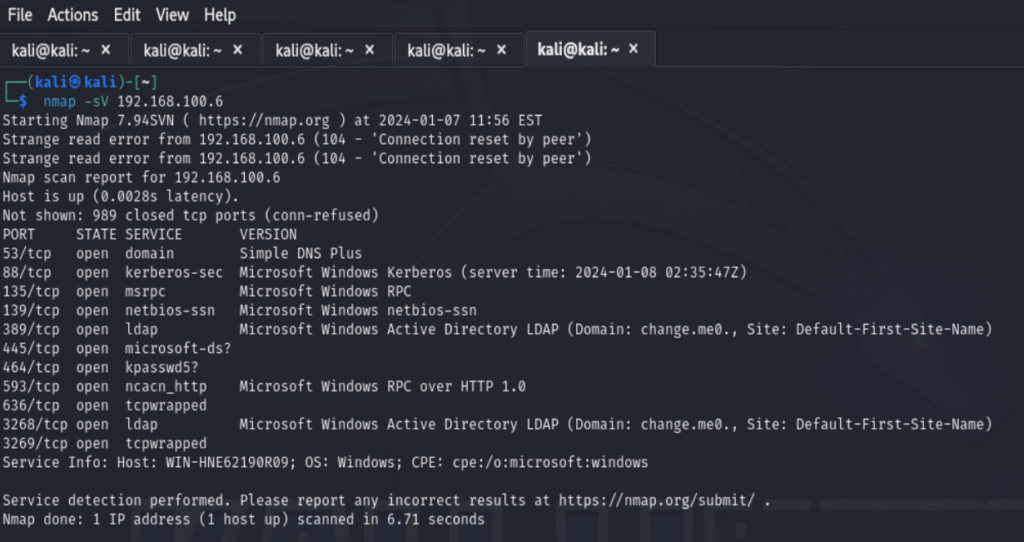
Lets get the IP from AD server by running `ipconfig` command.

From Kali we will launch nmap to get open ports.
Let us look for ldap anonymous query, to get namespace run following command:
ldapsearch -x -s base -H ldap://192.168.100.6 namingcontexts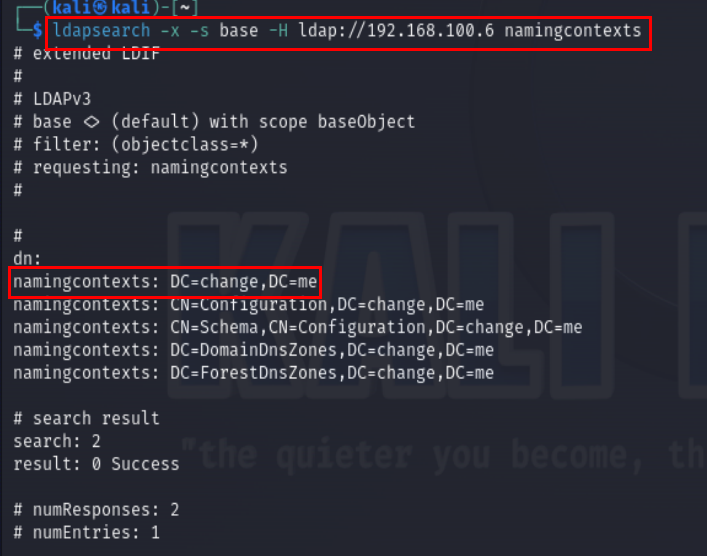
We can use this information for anonymous querying using following command:
ldapsearch -x -b "dc=change,dc=me" -H ldap://192.168.100.6 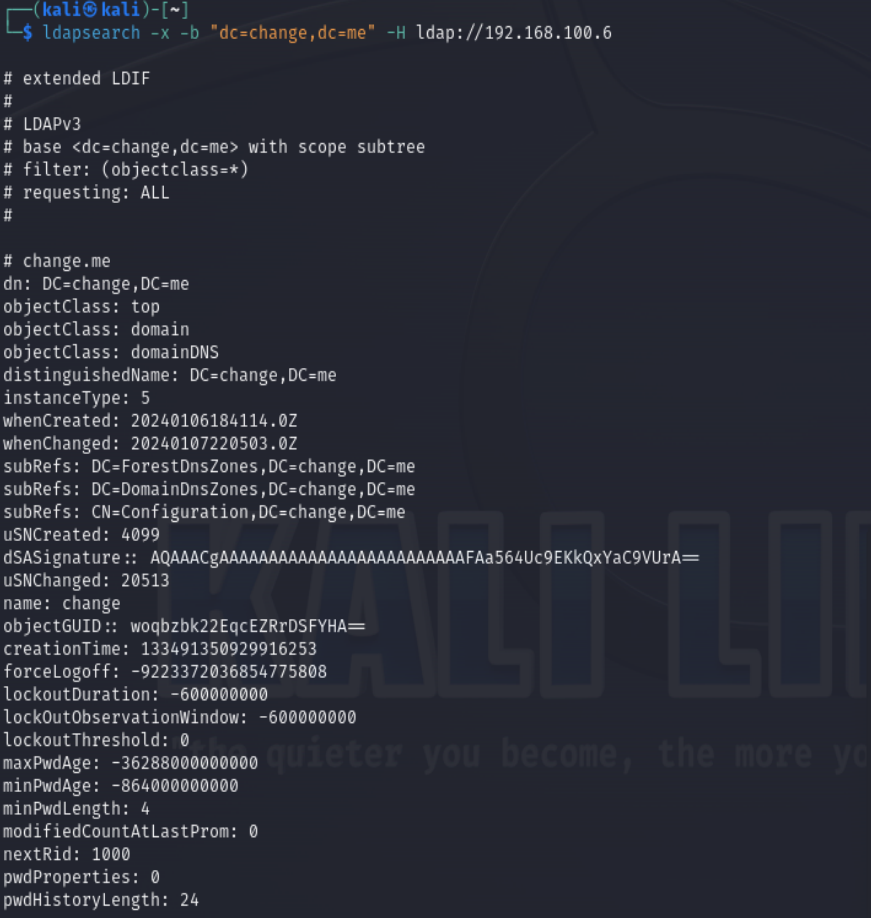
We can use grep to filter the results:
ldapsearch -x -b "dc=change,dc=me" -H ldap://192.168.100.6 | grep -i description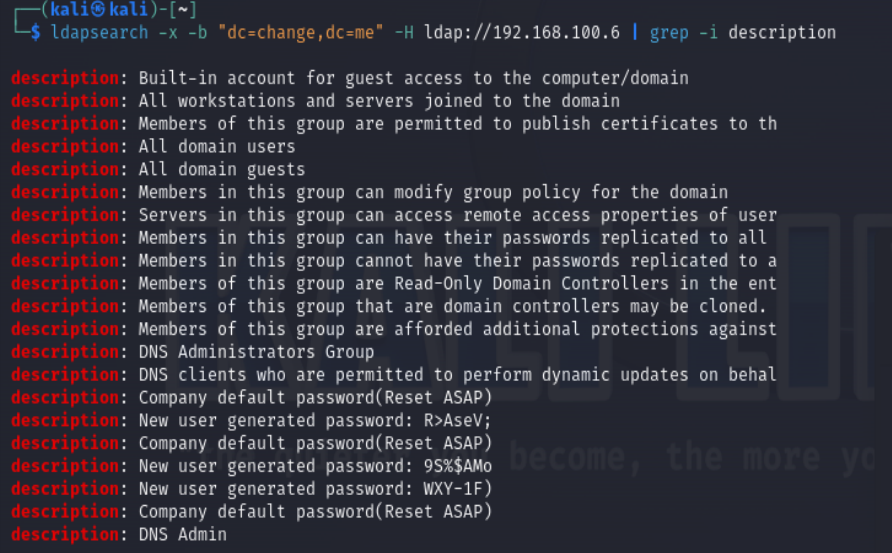
Nmap has script which allows us to get above info
nmap -n -sV --script "ldap* and not brute" 192.168.100.6 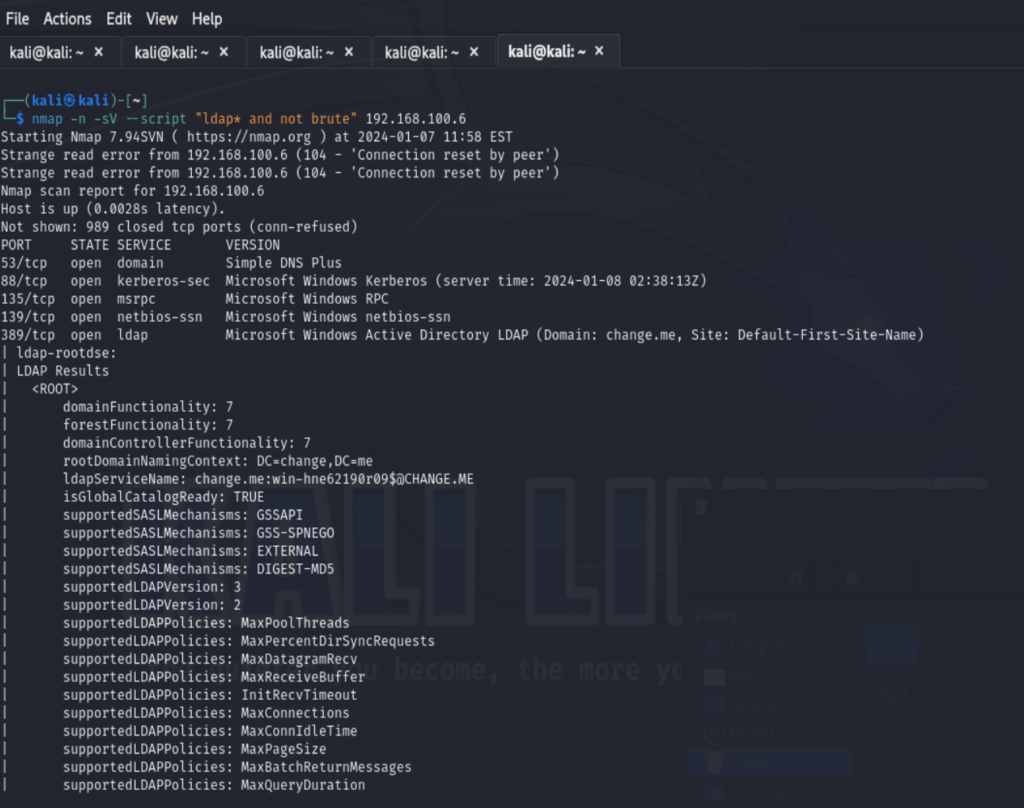
Following are the list of attacks that can be executed on this system:
- Anonymous LDAP query
- Abusing ACLs/ACEs
- Kerberoasting
- AS-REP Roasting
- Abuse DnsAdmins (…)
- Password in AD User comment
- Password Spraying
- DCSync (…)
- Silver Ticket (…)
- Golden Ticket (…)
- Pass-the-Hash (…)
- Pass-the-Ticket (…)
- SMB Signing Disabled
- Bad WinRM permission
- Public SMB Share
- Zerologon (Check version)
In our next post we will create a Active Directory network Lab, stay tuned!!